One of the confusing characteristics for companies seeking to deploy electronic signature (e-signature) solutions is differentiating offerings from diverse providers. Currently, numerous providers offer different e-signature schemes, with notable differences in their costs, interoperability, ease of use, legal acceptance, trust, and security. However, little documentation describes the different e-signature techniques to enable their comparison and assessment for their suitability in addressing specific business needs.
That said, it is necessary to identify the major features of each to assist technical architects and business managers in identifying the most suitable one for their business environments.
What is an E-Signature?
Throughout history, signatures have been used to identify individuals in different matters, such as business deals, finance, legal actions, government, and other transactions. Before the advent of the Internet and subsequent technological revolutions, signatures have always been handwritten. New personal identification methods have emerged as more processes become digitized.
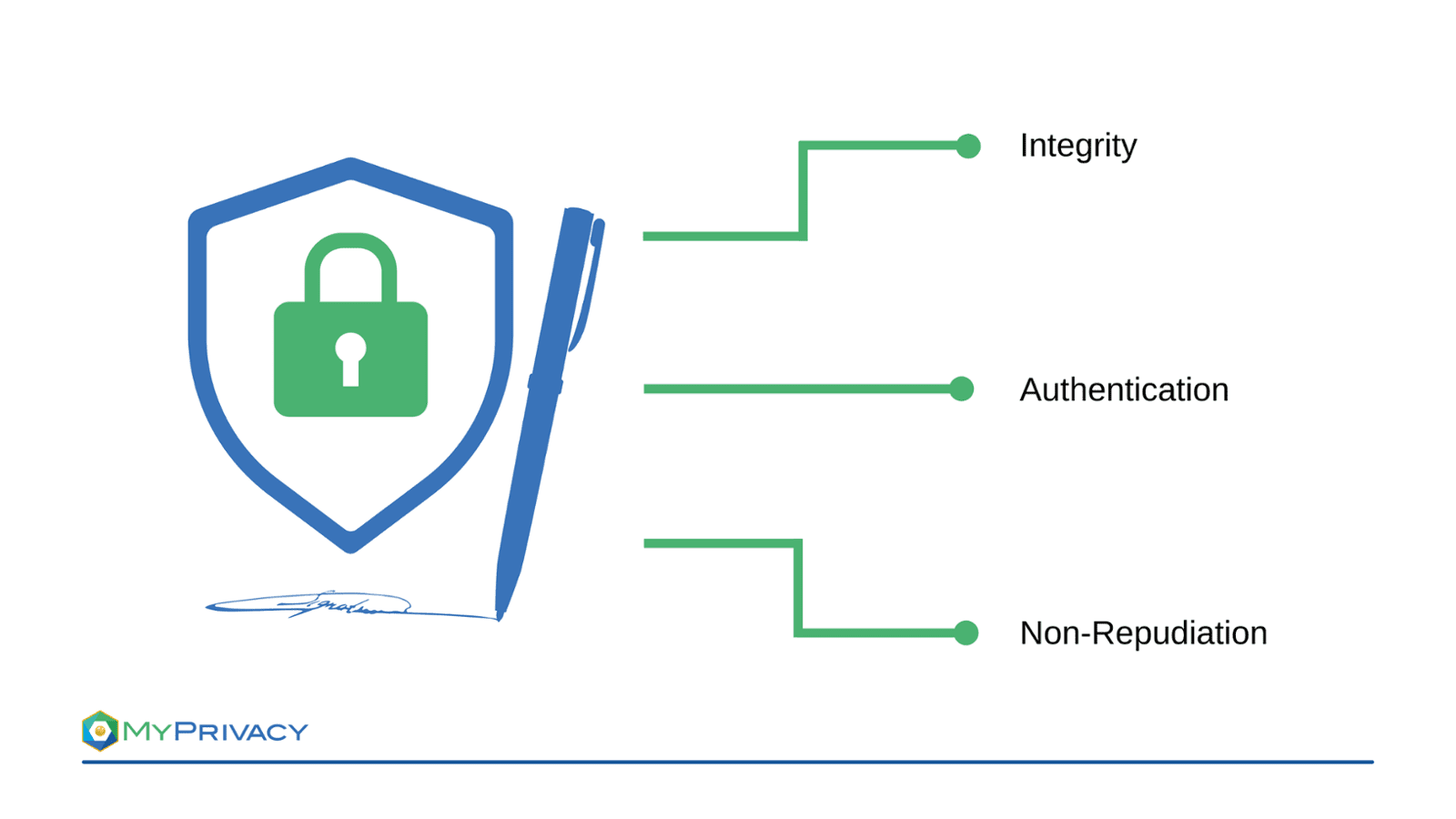
An e-signature is a depiction of users' supposed signature used to identify a person electronically. However, not everything referred to as e-signature is suitable for authenticating a user. The aim of this article is to provide an overview and highlight the differences. While a simple signature placed in e-mails can only be used to identify the sender, secure e-signatures can ensure integrity, authentication and non-repudiation:
- Integrity: The signature can be used to detect if changes to the signed data have been made afterwards.
- Authentication: The signature can be used to verify the signatory’s identity, since nobody else is able to create the signature.
- Non-repudiation: The signature can be used as evidence of consent to the signed data, since the signatory cannot deny that he signed himself.
Different Types of E-Signatures:
1. E-Mail Signatures
An email signature is anything that goes below an email body. Many email accounts leave the closing phrase, for example, 'best regards' followed by your name, as the default e-signature. It is nevertheless possible to implement different text or graphical content or upload an image to the email's footer. Email signatures often contain the sender's contact information, company or brand logo, or linked social media profiles.
Even though they are called signatures, they do not meet the previously listed characteristics of secure e-signatures. But, email clients such as Outlook are able to produce cryptographic signatures as well, if a corresponding certificate is installed.
2. Click-to-Sign E-Signatures
Click-to-sign e-signature comprises any mark placed on a digital document that indicates an individual's consent. Examples of click-to-sign e-signatures include providing an email address, typing in special script fonts, mouse squiggle, image upload, and drawing a signature on touch screen devices. Whereas click-to-sign electronic signatures are easy to use, they don't provide any security. Anyone with unauthorized access can easily copy the signatures from one digital document to another.
Click-to-sign E-signatures alone don't provide cryptographic protection to a signed document. As such, malicious actors can modify the contents in a digital document once a user appends a click-to-sign signature. Furthermore, the method does not contain any mechanisms for identifying a signer securely. A signatory can repudiate a signed document by claiming that the appended signature is fake or forged. In this regard, it is ill-advised to use click-to-sign signatures to sign sensitive documents or transactions. But this kind of solutions usually also embed a cryptographic signature into the final PDF document.
3. Cryptographic Signatures
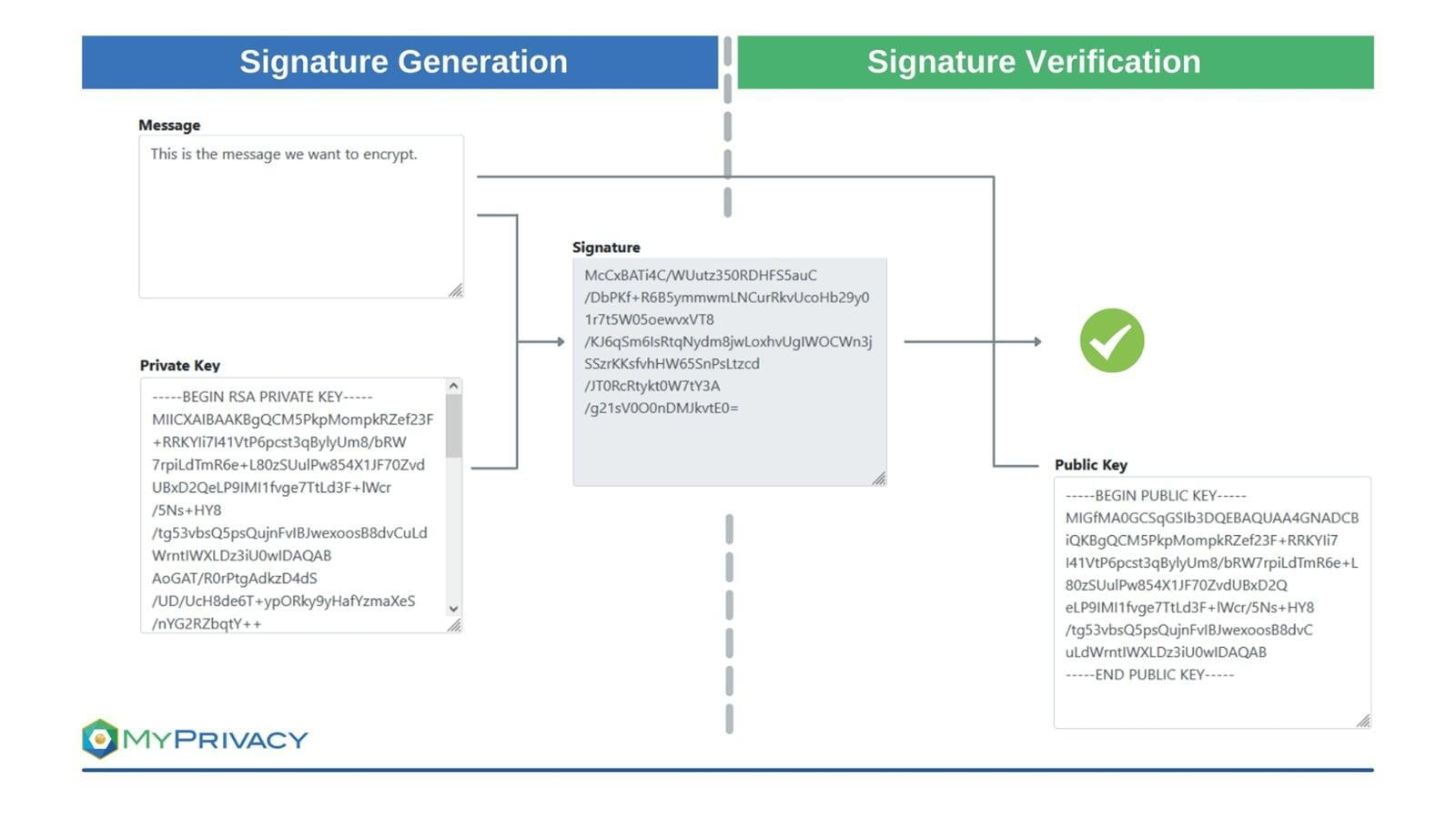
Cryptographic signatures consist of digital signature schemes that utilize mathematical algorithms to validate the integrity and authenticity of sent messages.
Cryptographic signatures work by creating a unique fingerprint of the data / message and combining it with the unique secret key (private key) of the signatory. The recipients of the data / message and the signature can use the signatories public key to verify the validity of the signature.
The following components are used in connection with secure cryptographic signatures:
- Cryptographic hash function: A hash function computes a fixed-length output from an arbitrary input, such as a document or email. A hash is referred to as one-way function: it is easy to compute the output value from the input value, but infeasible to find an input value matching a given output value. The output values can be seen as unique since it is infeasible to find collisions i.e. two different inputs giving the same output.
- Public key cryptography: this is an asymmetric encryption method that ensures the integrity of transmitted messages by using a sender's private key to create digital signatures. It hashes the messages and encrypts the hash values using the private keys. As such, message modification generates different hash values signifying the message has been tampered with. The public key cryptography can also be used to preserve message confidentiality by encrypting it using the recipient's public key. The recipient must provide the public key and own the corresponding private key to access and read the message.
4. Advanced Electronic Signature (eIDAS)
An advanced electronic signature provides each user with unique signing keys, thus offering the highest assurance and trust levels. The method permits anyone to verify signed documents using industry-standard PDF readers as it directly links a signed digital document to the user identity. It is using cryptographic signature to ensure that altering or modifying a signed document breaks the appended signature. Also, it binds a user's identity to a digital document preventing anyone else from signing on behalf of the legitimate user.
Advanced e-signatures offer robust security since they cannot verify digital signatures in digital documents with compromised integrity and confidentiality. Advanced e-signatures capture an individual's identity during an initial registration process and bind it to the signing certificate. It provides additional security checks since it performs deep checks with an accredited user identity provider. An organization or trusted certificate authority can issue the signing certificates.
5. Qualified Signature
A qualified e-signature is a special type of advanced e-signature scheme. Qualified signatures are designed based on the advanced electronic signature but provide additional requirements, offering a higher security level. Also, it has robust security since the verification and signing methods are standardized. A qualified and frequently audited certificate authority that conforms to standardized requirements must issue the user's certificate. Additionally, a Qualified Signature Creation Device (QSCD), which is verified tamper-resistant hardware, must be used to hold users' signing keys. The certified hardware devices are designed to provide optimal protection to prevent unauthorized individuals from accessing the signing keys. Therefore, attempts to dispute qualified electronic signatures created using specific keys are usually futile.
Cloud - A Comfortable Alternative?
Cloud signatures are one of the most recent methods used for signing documents and transactions remotely. In other words, cloud signatures are certificate-based, open digital signatures implemented over cloud networks. Companies use cloud signatures to digitally sign web and mobile devices using either qualified e-signatures or advanced e-signatures. Cloud signatures enable secure digital signing since they are backed by Trust Service Providers (TSPs) and certificate authorities that support the worldwide Cloud Signature Consortium (CSC).
Cloud signatures provide various benefits, first and foremost user convenience. The solution provides complete mobility to sign digital documents from any device with internet connectivity. Besides, using cloud-hosted signing services ensures the security of the users' signing keys. Cloud platforms store the users' signing keys in Hardware Security Modules. The security features ensure the preservation of a digital document's integrity and confidentiality since unauthorized changers render the signing keys invalid and unverifiable. Cloud signature services can also authenticate users using either multi-factor or single-factor mechanisms.
Be carefull which cloud signature-provider you trust. Whichever you choose, you need to be aware, that your keys are under the control of the chosen service-provider, which creates signatures on your behalf. A malicious service-provider could misuse the keys to produce signatures without your authorization.