Wir von MyPrivacy sind ein Team mit über 150 Jahren Erfahrung im Bereich sicherer Softwareentwicklung. Unser Unternehmen ist auf
Wir von MyPrivacy sind ein Team mit über 150 Jahren Erfahrung im Bereich sicherer Softwareentwicklung. Unser Unternehmen ist auf
innovative Kryptographie spezialisiert und erhielt unter anderem eine Seed-Finanzierung des Bundesministeriums und der aws
innovative Kryptographie spezialisiert und erhielt unter anderem eine Seed-Finanzierung des Bundesministeriums und der aws
(Austria Wirtschaftsservice) sowie eine Förderung der FFG (Österreichische Forschungsförderungsgesellschaft).
(Austria Wirtschaftsservice) sowie eine Förderung der FFG (Österreichische Forschungsförderungsgesellschaft).
Warum wir tun, was wir tun
Bei MyPrivacy widmen wir unser Wissen, unsere Arbeit und unseren Enthusiasmus der Lösung des Problems der Online-Privatsphäre und
Bei MyPrivacy widmen wir unser Wissen, unsere Arbeit und unseren Enthusiasmus der Lösung des Problems der Online-Privatsphäre und
Anonymität. Unsere Arbeit soll einen Beitrag zum sicheren Umgang mit Daten leisten und in erster Linie Menschen beim Übertragen ihrer
Anonymität. Unsere Arbeit soll einen Beitrag zum sicheren Umgang mit Daten leisten und in erster Linie Menschen beim Übertragen ihrer
sensiblen Daten vor bewusster und vor allem unerwünschter Überwachung schützen.
sensiblen Daten vor bewusster und vor allem unerwünschter Überwachung schützen.
Sensible Daten im Visier
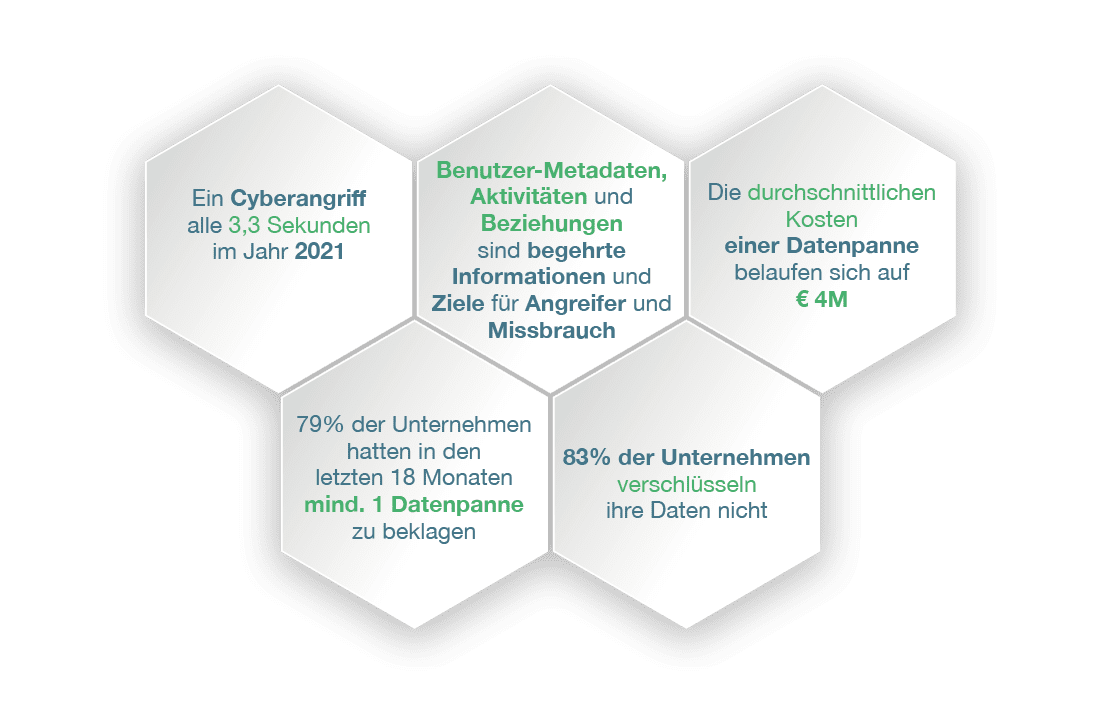
Jeder Mensch bzw. auch jedes Unternehmen hat sensible Daten, die nicht mit der Öffentlichkeit bzw. unbekannten Dritten geteilt werden
Jeder Mensch bzw. auch jedes Unternehmen hat sensible Daten, die nicht mit der Öffentlichkeit bzw. unbekannten Dritten geteilt werden
sollen. Neben dem Inhalt von Daten sind insbesondere auch Metadaten wertvolle Informationen, die unbemerkt erhoben werden und
sollen. Neben dem Inhalt von Daten sind insbesondere auch Metadaten wertvolle Informationen, die unbemerkt erhoben werden und
bereits über vieles Auskunft geben können. (Wer?, Was?, Wann?, Wo?, Wie oft?, Mit wem?...)
bereits über vieles Auskunft geben können. (Wer?, Was?, Wann?, Wo?, Wie oft?, Mit wem?...)
Nutzer selbst und teilweise auch staatliche Behörden haben ihren Fokus auf den Schutz von digitaler Identität und Anonymität gelegt.
Nutzer selbst und teilweise auch staatliche Behörden haben ihren Fokus auf den Schutz von digitaler Identität und Anonymität gelegt.
Der kollektive Wunsch der Nutzer nach mehr Privatsphäre wird immer lauter.
Der kollektive Wunsch der Nutzer nach mehr Privatsphäre wird immer lauter.
Was macht MyPrivacy
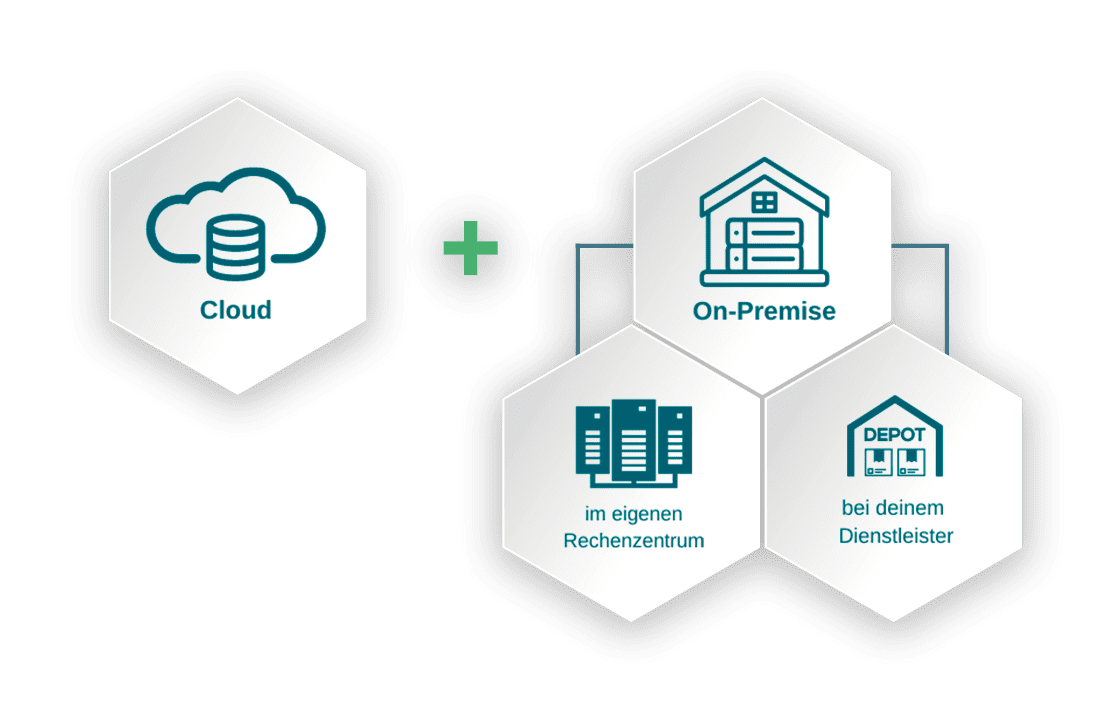
Es werden immer mehr Daten über Cloud-basierte Plattformen ausgetauscht. Dabei wird dem Cloudanbieter blind vertraut, dass er sie
Es werden immer mehr Daten über Cloud-basierte Plattformen ausgetauscht. Dabei wird dem Cloudanbieter blind vertraut, dass er sie
nicht nur vor Angreifern beschützt, sondern auch selbst nicht missbraucht. Verschlüsselung hilft nur dabei, Daten für Unbefugte dauerhaft
nicht nur vor Angreifern beschützt, sondern auch selbst nicht missbraucht. Verschlüsselung hilft nur dabei, Daten für Unbefugte dauerhaft
zeitlich begrenzt zu verschleiern, verhindert jedoch nicht, dass Cloudanbieter systematisch Metadaten über die Benutzer sammeln,
zeitlich begrenzt zu verschleiern, verhindert jedoch nicht, dass Cloudanbieter systematisch Metadaten über die Benutzer sammeln,
analysieren und für eigene Zwecke nutzen.
analysieren und für eigene Zwecke nutzen.
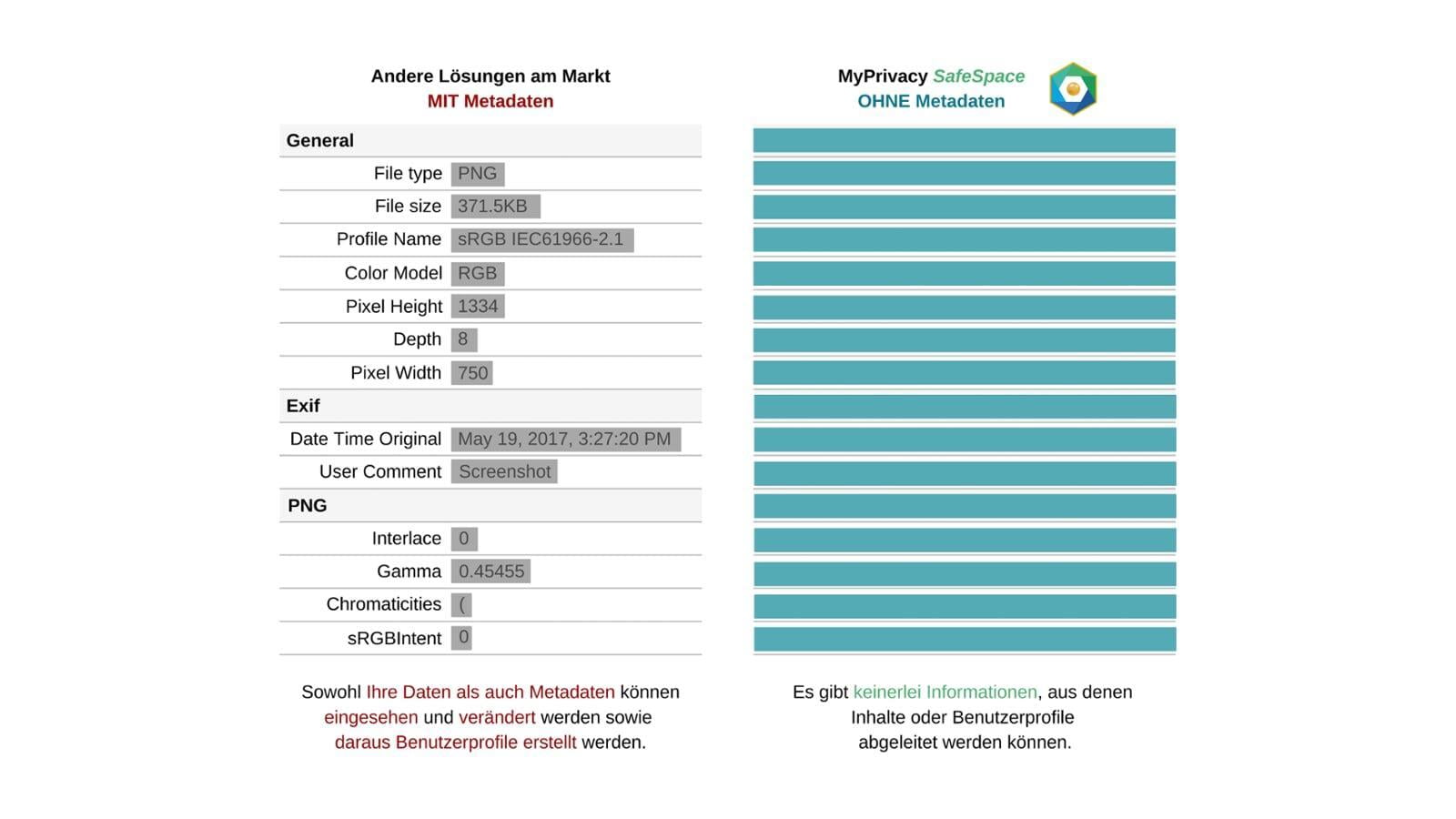
Was sind Metadaten?
Metadaten enthalten wertvolle Informationen über die Daten. Sie können aus den Daten abgeleitet werden wie etwa die Größe oder das Format oder während der Verarbeitung der Daten festgehalten werden, z.B. der Autor und das Datum der letzten Änderung.
Zugriffsrechte auf die Daten d.h. welche Benutzer dürfen die Daten lesen, schreiben oder löschen, gehören auch zu den Metadaten. Auch wenn die Daten verschlüsselt sind, sind es Metadaten in der Regel nicht und können oft aufschlussreicher sein als die Daten selbst.
Aus den gesammelten Metadaten können Cloudanbieter und Hacker aussagekräftige Benutzerprofile erstellen und diese zu ihren Zwecken nutzen.
Unser Produktportfolio
Wir bieten effektive Lösungen zum Schutz von Personen und Unternehmen vor unerwünschter Überwachung bei Datenaustausch
und Speicherung. Unsere patentierte Technologie schützt nicht nur die Daten der Benutzer, sondern auch sämtliche Benutzer-
Aktivitäten sowie die Einsicht in ihre Berechtigungen. Unsere Technologie trägt den Namen SafeSpace. Mit SafeSpace setzen wir neue
Maßstäbe für den Schutz von Daten und die Privatsphäre der Nutzer.
Für mehr Informationen zu unseren Produkten,
besuchen Sie die einzelnen Produktseiten.
besuchen Sie die einzelnen Produktseiten.