How does it happen and what are the damages?
- What is a Data Breach?
- Reasons for Data Breaches?
- Different Types of Cyber Attacks
- What are the damages of Data Breaches?
- Are Data Breaches on the Rise?
What is a Data Breach?
A data breach is an incident that exposes confidential, sensitive, or protected information to unauthorized people, services, or machines. Simply put, a data breach allows entities to view, share, modify, or destroy files and data without permission. Cybercriminals target systems to steal sensitive, confidential, or proprietary information, such as customer data, credit card numbers, trade secrets, health information, or national security details.
Reasons for Data Breaches?
In today's world, people and organizations use computers and mobile devices with advanced connective features. At the same time, developers release new technologies and applications faster than security measures can protect them. Maturing underlying technologies has resulted in an increase in devices in the internet of things (IoT) space to offer users convenience. According to McKinsey and Company, the number of enterprises that use IoT technologies has increased from 13 percent in 2014 to about 25 percent today. The worldwide number of IoT-connected equipment is projected to increase to 43 billion by 2023, an almost threefold increase from 2018.
The increased adoption of technology, however, adds more places for sensitive information to slip through. Billions of devices in the IoT sector and broader application of cloud and mobile technologies introduce gaping flaws that hackers exploit today. Besides, data breaches keep growing as organizations release new products, tools, and services with minimal security testing. In the end, governments, organizations, and individuals are now at risk. Unprotected individuals or companies put others at risk as well.
Apart from software and hardware, data breaches happen due to weaknesses in user behavior. Some users still have poor digital habits that can lead to compromise of a company system or network. An EC-Council blog post reveals that employee negligence is the number one cause leading to cyberattacks. With companies adapting to remote work since COVID-19, and arguably for the foreseeable future, insider threats will be responsible for 33 percent of breaches in 2021, up from the estimated figure of 25 percent of all incidents in 2020. A recent survey by Deloitte of 535 Austrian private sector decision-makers showed that since mid-March 2020 Austrian COVID-19 lockdown measures, 40 percent of organizations increased employee use of personal devices, opening more cybercrime gaps. Sixty percent of Austrian private organizations perceive their employees as an increasing risk factor.
How does a Data Breach occur, and what are the Goals of Cyberattacks?
A data breach occurs when a cybercriminal infiltrates a system, server, or data source and extracts confidential and sensitive information. Hackers assess computers or networks to bypass network security and steal, modify, or destroy files. Apart from cybercriminal instigated data breaches, other incidents arise from insider leaks, loss or theft of digital devices, or human error.
Different Types of Cyberattacks
Hackers use different strategies and tactics that prove effective in stealing confidential information and disrupting systems. It helps to understand various cyberattacks that hackers use to harm an organization. They include:
- Malware: Harmful software, such as ransomware, spyware, viruses, and trojan horses, that wreak havoc in systems and devices, including taking control of the computer, monitoring user activities, installing other harmful programs, locking system access, and sending confidential information to a remote server.
- Phishing: More often than not, attackers understand that users will open attachments or links with compelling reasons for them to take action. In effect, they send emails pretending to be someone else to trick unsuspecting employees into taking an action that they normally wouldn't.
- SQL Injection: Many servers hosting confidential data use structured query language (SQL) to manage databases. Hackers launch SQL injection attacks targeting these database systems to trigger servers to divulge information.
- Cross-Site Scripting: Hackers opt for cross-site scripting attacks to target website users. They inject malicious code to run in the browser when victims visit vulnerable websites. In most cases, hackers embed links into malicious JavaScript in a commend on a website.
- Denial of Service (DoS): Cybercriminals also deploy tactics and tools that flood websites with more traffic than they can handle, making it nigh-impossible for servers to respond to requests from genuine visitors.
What are the Damages of Data Breaches?
Cyberattacks' total cost can be a lasting issue for an organization's systems, data, reputations, and finances. Simply stated, data breach impacts come in the form of damage to the victim's reputation because of a perceived breach of trust or financial losses from penalization and compensation fees. The following issues can result from a data breach:
- Data Loss: unquestionably, cyberattacks can lead to data loss. Incidents involving the compromise of confidential data are among the common cyber incident forms. Hackers deploy tools and tactics that enable them to illegally access, modify, transfer, or destroy victims' financial data, customer information, trade secrets, and intellectual property. In other cases, employee error, such as loss or disposal of a hard drive containing confidential information, can result in data breaches.
- Reputational Damage: a data breach can have a devastating effect on a company's reputation. Organizations like Marriot, Twitter, Zoom, Target, and SolarWinds that have been victims of cyberattacks have suffered brand image damage as many people associate them with the data breach itself rather than their actual business operations. Reputational damage could, in turn, lead to loss of customers and sales and reduction in profits. Along with that, the destruction of brand image can impact suppliers and relationships with partners, investors, and third-parties vested in a business.
- Financial Loss: data breaches result in substantial economic costs from the theft of company data, leakage of financial details, theft of money, disruption of business operations, and loss of business or contracts. Besides, cyberattack victims incur costs associated with repairing affected networks, systems, and devices.
- Legal Consequences: Data protection and privacy laws, such as the General Data Protection Regulation (GDPR) and Trade Secrets Protection Act, require organizations to ensure the security of all personal data and trade secrets in their possession. In case hackers or insiders compromise systems and sensitive data, victims may face regulatory sanctions and fines.
A recent IBM study found the global average total cost of a data breach at $3.86 million in 2020. Healthcare has the highest industry average cost at $7.13 million. The same report indicates that customer personally identifiable information (PII) has the most increased cost per record, averaging $150. COVID-19 also had an impact on the cost of cyberattacks during the same period. Remote work became a primary security consideration. The study reveals that remote work's impact on the average cost of a data breach is $137,000.
On the other hand, the time an organization takes to detect and contain a cyber incident affects a data breach's cost. The same study revealed, that the average time to identify and contain a data breach, commonly referred to as the breach lifecycle, was 280 days in 2020. An organization benefits from $10 million average savings from managing a breach in less than 200 days.
Are Data Breaches on the Rise?
Data breaches are now a never-ending story as we continuously hear about many small and large organizations being compromised. The year 2020 proved to be a period of contradictions, with the cybersecurity field experiencing a wide gap between reality and perception. The volume of records compromised last year jumped by 141 percent to a whopping 37 billion records, the largest number recorded in the previous 15 years. The number is undoubtedly higher, considering that not all organizations that suffer a data breach disclose it publicly, while others underreport the numbers.
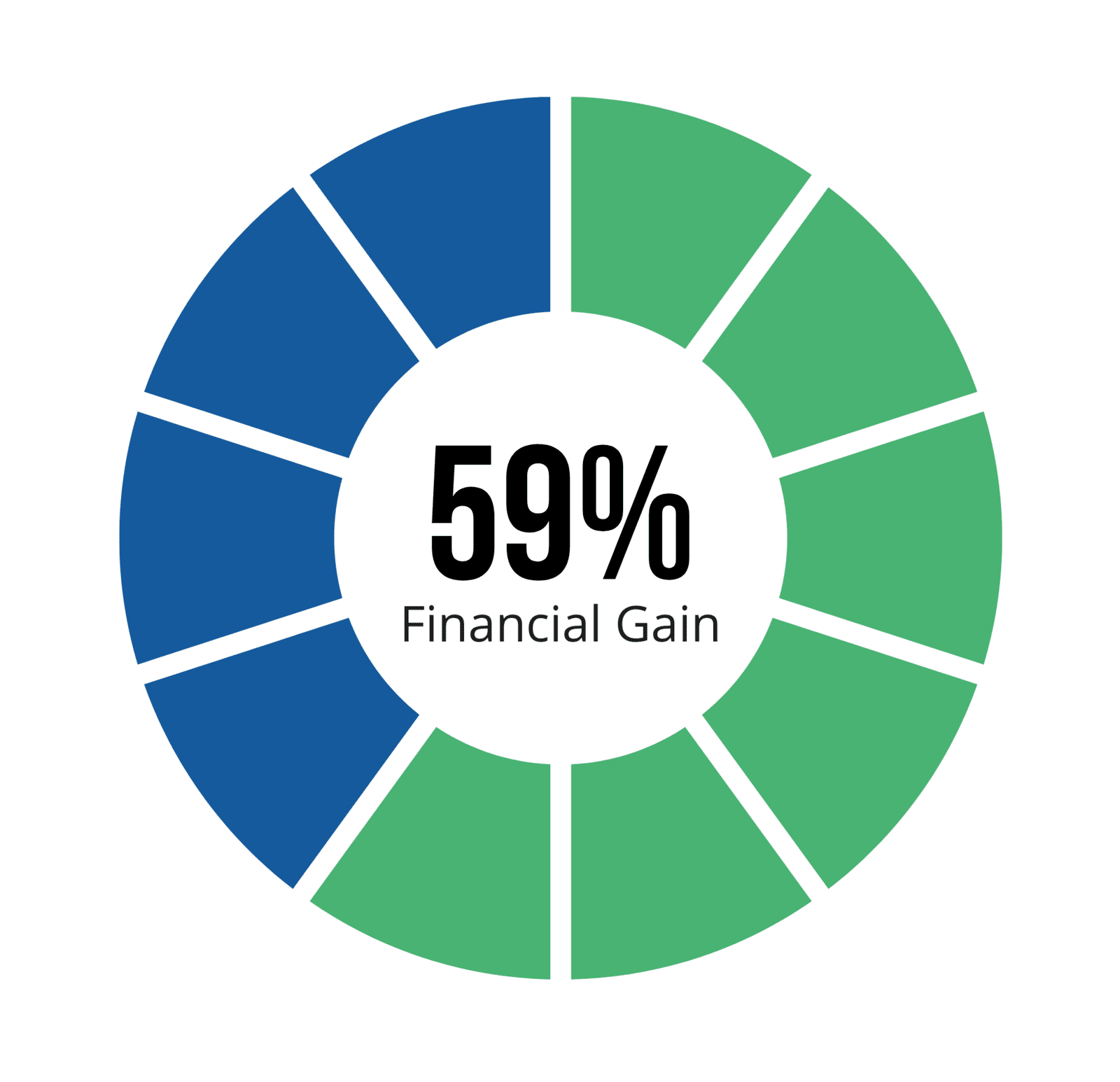
The current COVID-19 pandemic has put industries, especially the healthcare sector, under pressure. Hackers are riding on the situation to target organizations, with the number of ransomware incidents targeting the industry increasing during the pandemic. This observation explains why 86 percent of breaches in 2020 were financially motivated, and 10 percent were motivated by espionage.
No matter what a post-COVID workplace looks like, increased security risks must be addressed and mitigated. As dynamics have shifted and the world changes, private individuals and organizations too must adapt. The growing number of data breaches from cyber-attacks force us to rethink security and protect sensitive content to the highest standards.